Importance of Secure and Robust OTA Updates for Embedded Linux Systems
Do you have a fleet of IoT devices deployed in different locations and want to update their system/ software, debug for issues, and monitor their system status? Well…This is where OTA updates come in action!
What is an OTA Update?
Over-the-air update is an update where there is a central server and this server is pushing software or system updates to other devices which are located remotely.
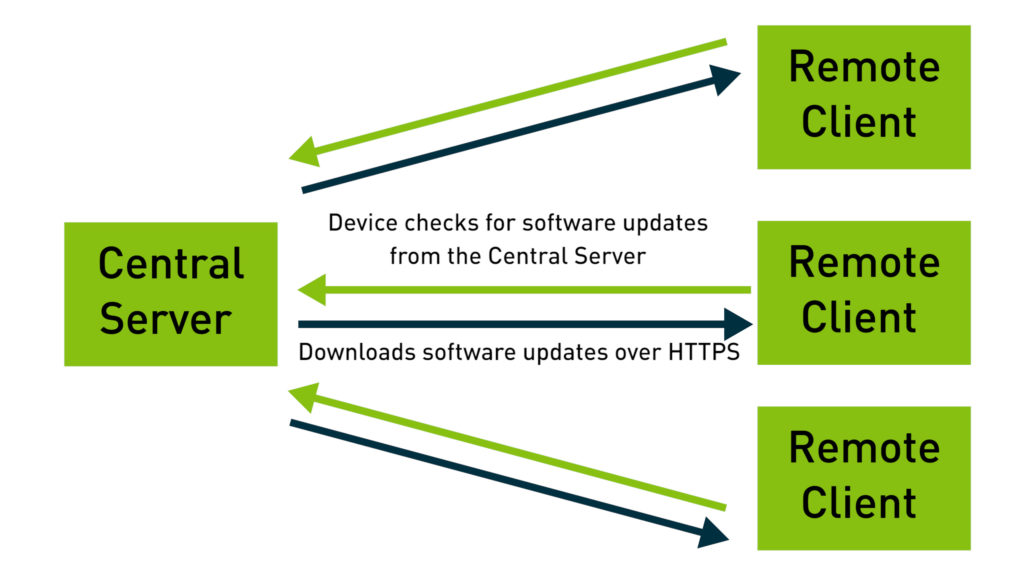
The remote devices report to the server periodically to check for updates. If there is a software update available for a particular device, the remote device downloads the update and installs it.
Why do we need an OTA update service?
Update devices remotely:
If you have many devices located at different locations, and you want to update them, it would be a very troublesome process to visit each device physically and update them. Updating the devices over-the-air can solve this.
Configure device remotely:
The same applies if you want to do some device configuration. By having an OTA update service, you can easily configure them remotely.
Troubleshoot devices remotely:
If you need to access the devices via a terminal or transfer files to remote devices, you can also do that by using an OTA update service.
Monitor devices remotely:
Finally, you can easily monitor remote devices for their working status by using an OTA update service.
What we need to consider when choosing an OTA update service?
We mainly need to consider two important aspects when choosing an OTA update service and they are:
- Security
- Robustness
Security
We really need to be careful about security when performing OTA updates to remote devices. If proper security measure is not taking when performing the update, it is probable for the remote device to get exposed to vulnerability such as hacker attacks. Most of the OTA update services provide secure OTA updates by using HTTPS protocol to perform the updates. This means the certificates on the remote device should match with the certificates on the update server in order to establish the connection. Also, some OTA update servers support code signing, which means, after we specify that the server is a trusted party, only after that the remote device will accept the update.
Robustness
On the other hand, it is very important to make sure that the update system is robust because the devices are deployed remotely, and it will be a troublesome process in the event that the device stops working and need to physically be present at the device to fix it. This could happen when you update a device over-the-air and the device power gets cut off in the middle of the update or else, the update failed for some other reason. To avoid this kind of breakdowns, proper measures should be set on the update system so that in the event of a breakdown during an update, the remote devices can restore the system to a previous working state.
Using Mender as an OTA Update Service
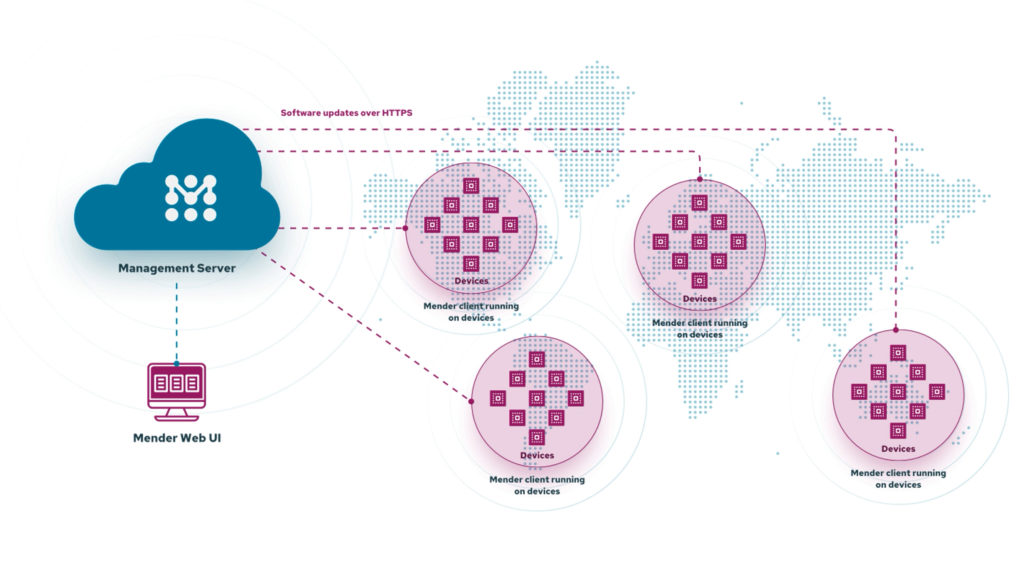
Mender is a secure and robust software update system designed to handle large number of devices. It has a simple client and server architecture allowing central management of deployments to all devices.
Click here to sign up and connect up to 10 devices free for 12 months!
Security and Robustness of Mender
As I have explained previously, on the security side, Mender push OTA updates by using HTTPS to make the update process more secure. Also, Mender support code signage when pushing updates to remote devices.
On the robustness side, Mender stands out because of its dual A/B rootfs partition layout. Basically, when you generate a system image for the very first time with Mender client integration, the system partition layout will be as follows.
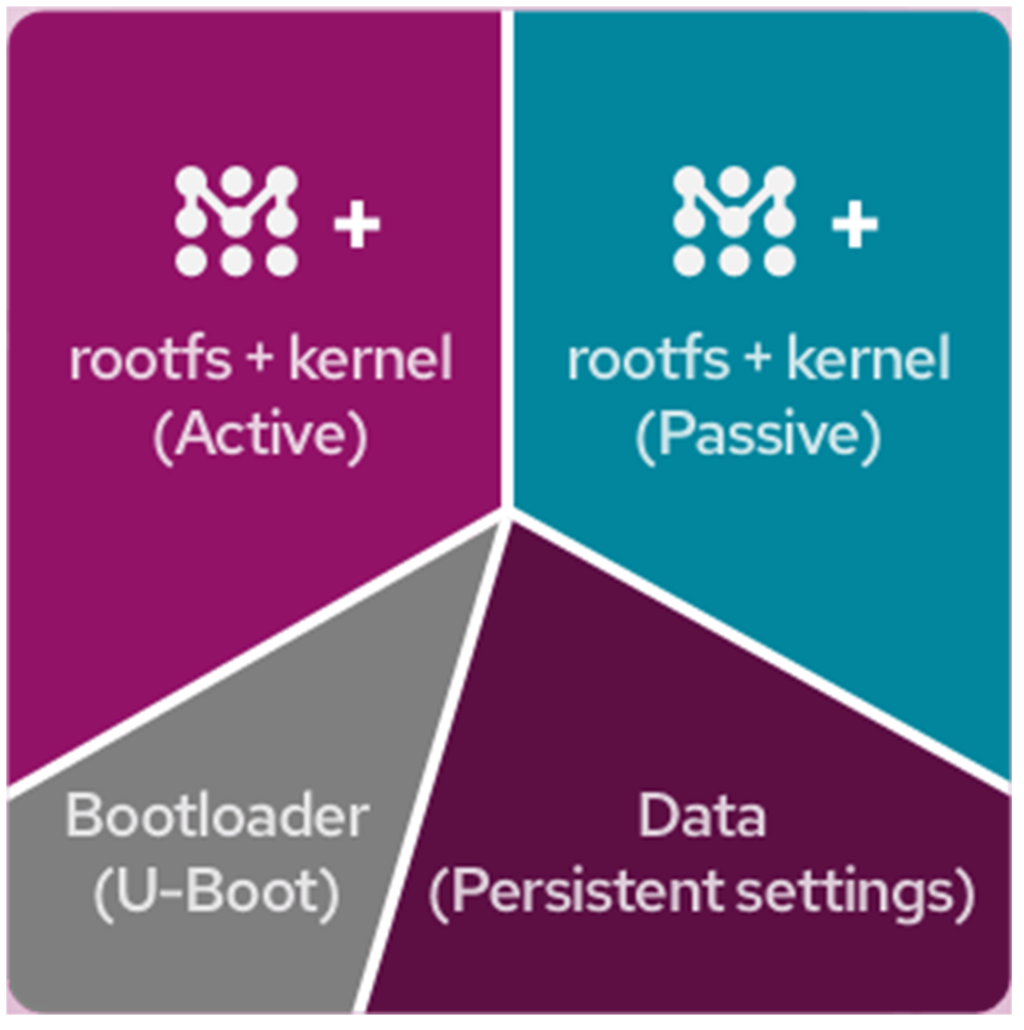
As you can see, it creates two rootfs+kernel partitions which are duplicates of each other. Active partition is the partition that it uses when you boot the system for the very first time.
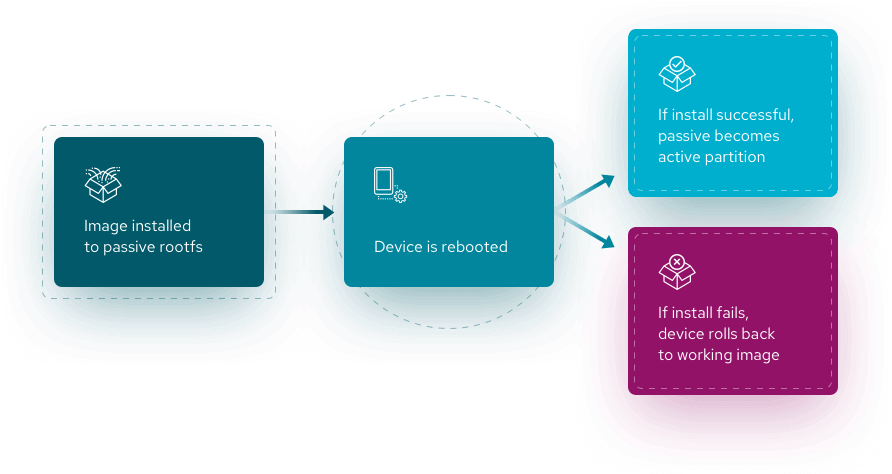
When you push an update from the Mender server to the remote device, mender client on the device will download the image and write the image to the rootfs partition that is not running. Then it will configure U-Boot to boot from the updated rootfs partition.
vAfter that the device will reboot and try to boot from the updated partition. If the update gets corrupted due to power loss during the process or due to any other reason, the device will boot from the original partition that was running before. This will ensure that the device will be booted exactly the way it booted in the original working state.
If the update succeeds, the update partition will be set to boot permanently when mender starts as part of the boot process. Now the previous passive partition has become the active partition.
Seeed SBCs supporting Mender
Mender.io has established a new partnership with Seeed to provide their community of makers and professional embedded developers with an integrated OTA software updates capability solution for 4 of its hardware boards.
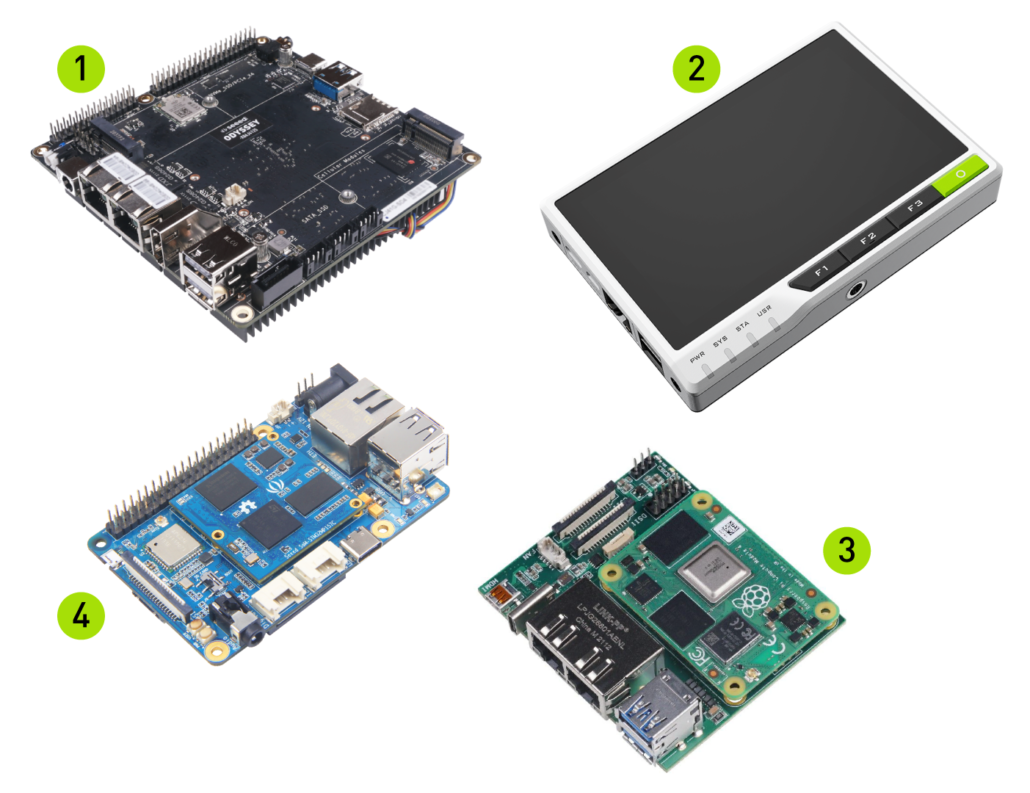
We integrate mender client to these boards along with their existing image compilations using the Yocto Project.
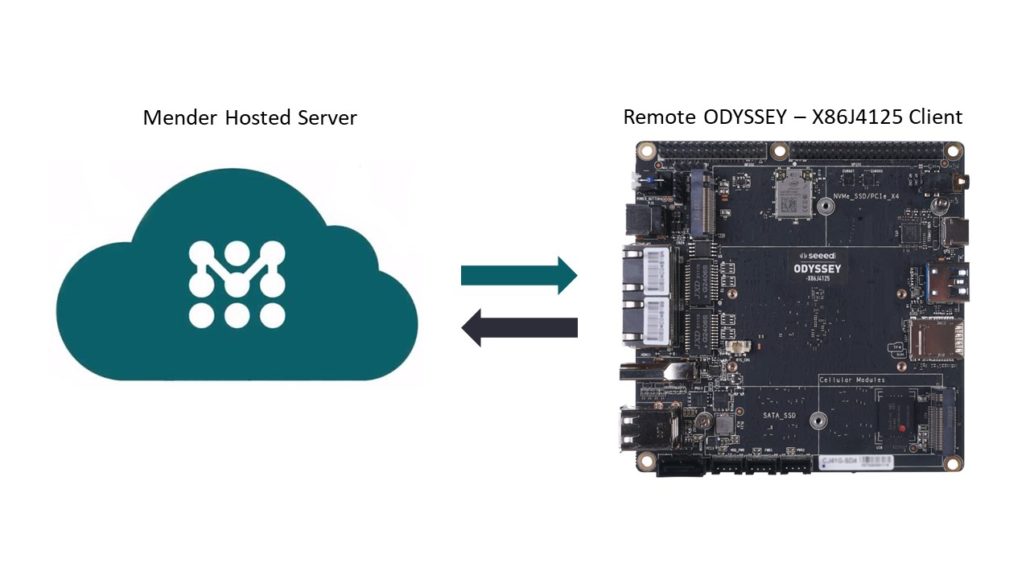
We have already finished Mender Client and Self-Hosted Mender Server integration for the ODYSSEY – X86 board. You can learn more about them below:
Mender Client on ODYSSEY – X86
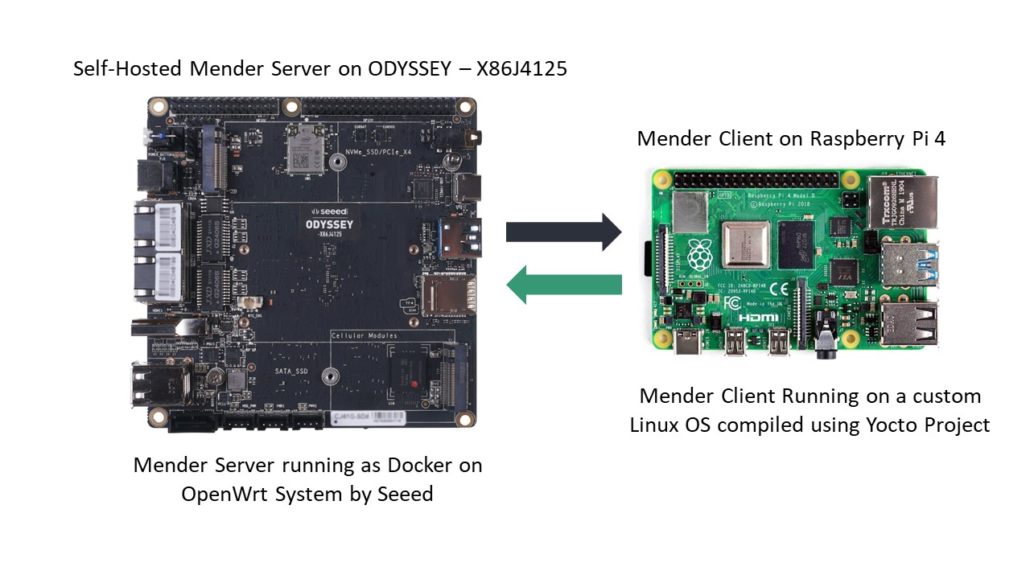
Self-Hosted Mender Server on ODYSSEY – X86
We have also prepared a video. Please check below:
OTA Updates for Azure IoT Hub with Mender.io
You can also use Mender to update Embedded Linux Systems which are connected with Azure IoT Hub. The below video explains about this and also demonstrates the use of Mender with Azure IoT Hub by showcasing a demo.
OTA Integrations for reTerminal, ODYSSEY – STM32MP157C and Dual Gigabit Ethernet Carrier Board for RPi CM4
In the coming weeks, 3 further board integrations from Seeed with Mender OTA will be launched with accompanying tutorials published on the Mender Hub and the Seeed Wiki. These boards are the reTerminal, the ODYSSEY – STM32MP157C, and Dual Gigabit Ethernet Carrier Board for Raspberry Pi Compute Module 4.